StarTree Cloud Deployment Models: BYOC vs Public SaaS


Intro to StarTree Cloud
Apache Pinot™ has established itself as a comprehensive, real-time analytics platform for building mission-critical analytical solutions across different companies and industry segments. StarTree Cloud, powered by Apache Pinot, is a Database-as-a-Service (DBaaS) that provides a fully managed experience for deploying and operating this powerful platform, allowing you to focus on the most important part — elevating the experience for your customers.
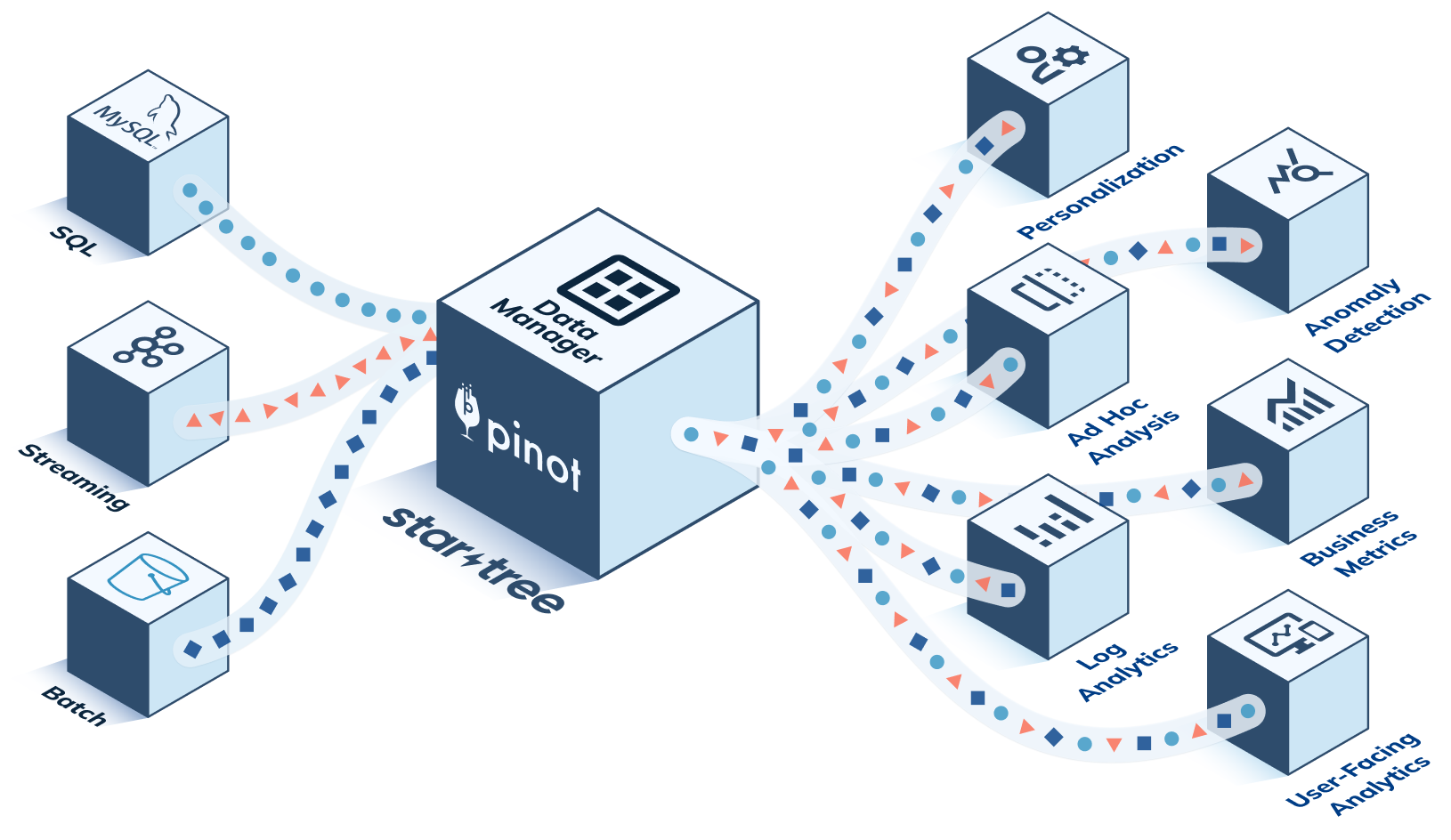
Fig 1: High-level view of StarTree Cloud
One of the biggest challenges of providing this cloud service is ensuring trust in the customer’s data. Although a traditional Software as a Service (SaaS) model can provide the necessary security guarantees, there are certain kinds of customers that don’t want to send the raw data out of their cloud network. To address this, StarTree Cloud comes in 2 deployment flavors to satisfy the varying requirements of different customers.
Public SaaS: A traditional SaaS edition of StarTree cloud is great for customers who want a low-touch experience and prefer a hassle-free, convenient SaaS service.
Bring Your Own Cloud (BYOC): Also called Private SaaS, this edition of StarTree Cloud caters to customers who want additional control over how data is managed and stored.
In this blog, we will look at how StarTree built a common software stack to support these deployment models. We will also look at the challenges of providing the BYOC experience and discuss our approach to addressing the same.
Public vs BYOC editions of StarTree Cloud
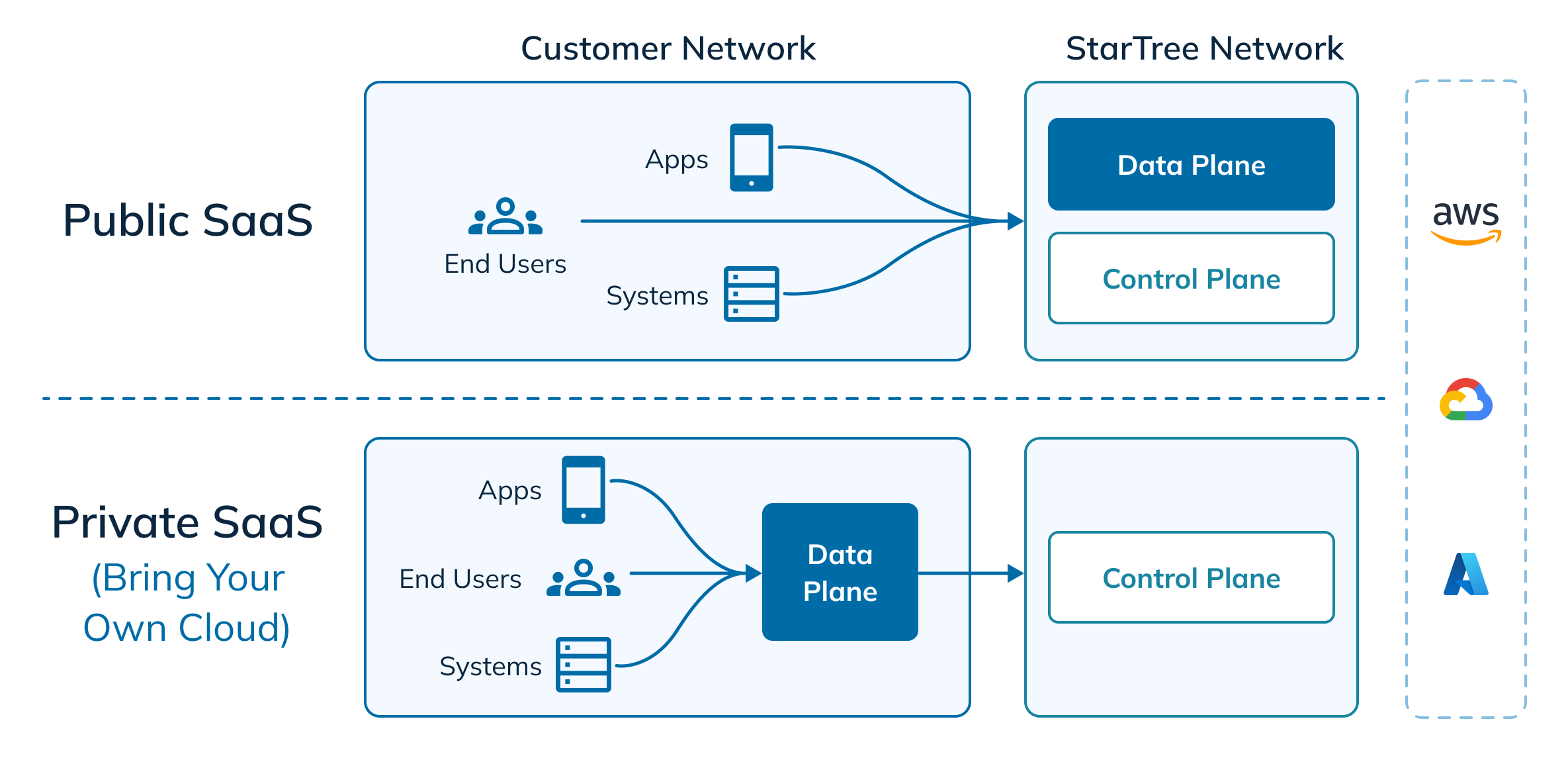
Fig 2: Public vs BYOC editions of StarTree Cloud
There are 2 main components of StarTree Cloud:
Data Plane: All the components required for data collection, management, and query processing along with the value-added services and tools
Control Plane: Responsible for deployment, management, and coordination across all StarTree data planes.
In a Public SaaS configuration, both the StarTree control plane and data plane are deployed in the cloud network managed by StarTree. In this case, data and queries from your cloud network are sent to the StarTree cloud network. In contrast, BYOC enables deploying the StarTree data plane in your cloud network so that it’s co-located with your other data systems and applications. In this case, the StarTree control plane remotely manages the data plane.
Benefits of StarTree’s Public SaaS offering
Fully hands-free: You don’t need to be involved at all in administering the data plane.
Simpler setup: You just focus on your data, your schema, and queries.
Isolation guarantee: Your SaaS instance is isolated from noisy neighbors from infrastructure as well as the Pinot cluster point of view.
Benefits of StarTree’s BYOC offering
Following are the key features why a lot of customers demand the BYOC experience with StarTree Cloud:
Compliance & Data Security: Data never leaves the customer’s security perimeter. Customers have full control over who gets access to the data as well as adhere to their data compliance and governance standards.
Fully managed: Customers get a comprehensive SaaS-like experience without the need for any in-house expertise. They don’t need to worry about deployment, upgrades, and routine cluster maintenance.
SLA: Customers get the same SLA guarantees as that of a traditional SaaS deployment. Although this introduces additional challenges for StarTree (see below), there is no difference in the experience from a customer’s point of view.
Flexibility: Since infrastructure is deployed in the customer’s environment, they can choose from a variety of supported compute and storage instance types and advanced customizations.
Cost savings: Allows the customer’s cloud savings plan to be applied towards this infrastructure.
No persistent connection is needed between the control and the data plane.
StarTree Cloud Architecture
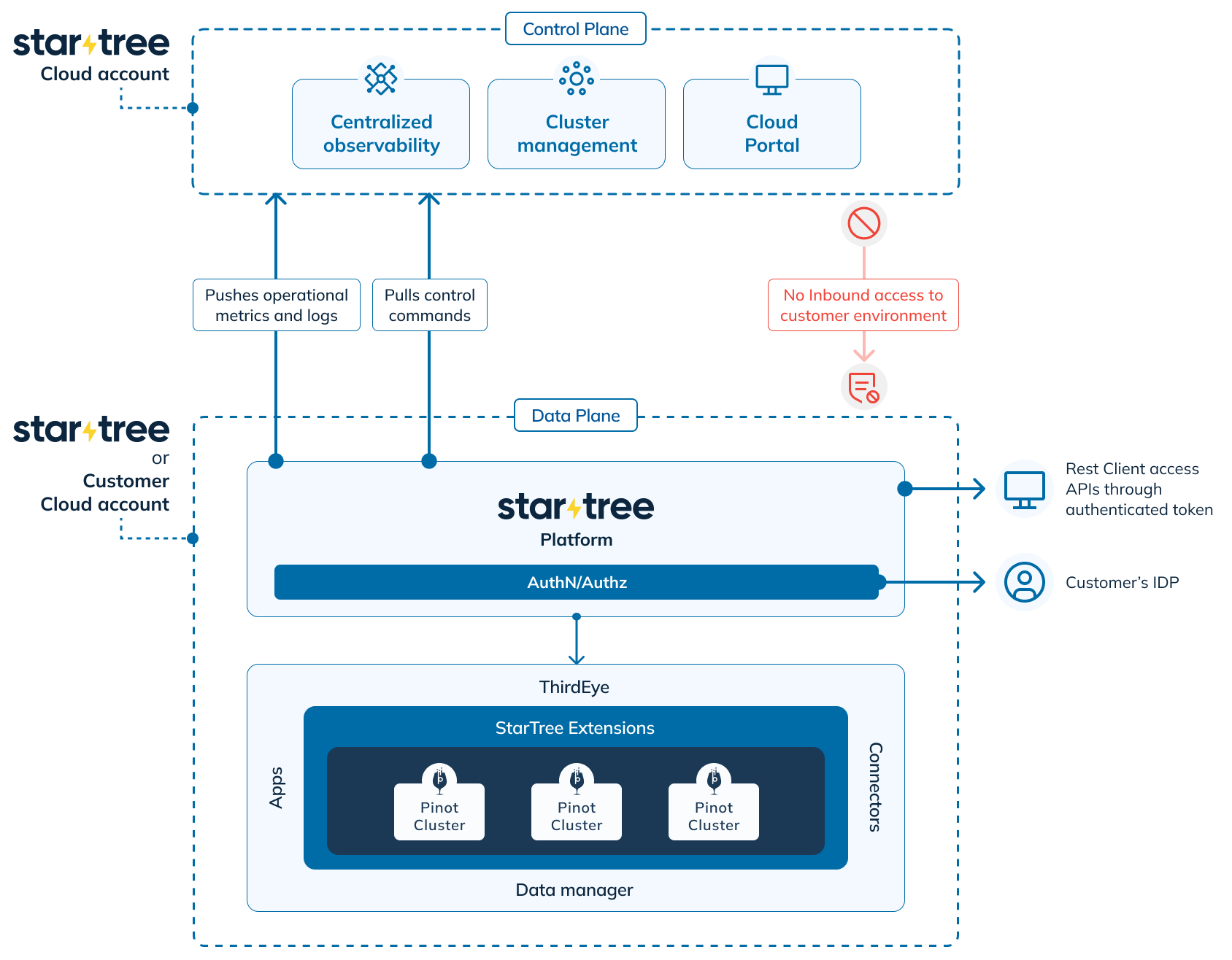
Fig 3: High-level architecture of StarTree Cloud
Figure 3 depicts the high-level architecture of StarTree Cloud which is used in both BYOC and Public SaaS deployments. Let’s look at the components in greater detail.
Data Plane
As depicted in Fig 4, The StarTree Data plane consists of various services and utilities associated with the customer’s data. The components are as follows:
Apache Pinot cluster: An Apache Pinot cluster deployed using a StarTree-certified build process with the recommended configuration from StarTree experts.
StarTree Extensions: Proprietary StarTree extensions that enhance the core Pinot functionality in order to make it cheaper, faster, and easier to operate. Examples include StarTree Cloud Tiered Storage, new indexing strategies (Sparse Index) and so on.
Value Added Services: This includes
Data Manager: Self-service data ingestion tool for allowing users to fetch data from various sources (streaming/batch/SQL), perform data wrangling, and also customize advanced Pinot config via an intuitive UI
StarTree ThirdEye: Our flagship application for detecting real-time anomalies on time-series data stored in the Pinot cluster as well as performing interactive root cause analysis on multi-dimensional data.
Connectors: Includes various connectors and libraries required for ingestion and data dispersal.
Tooling: Utilities required for things like data migration, advanced cluster operations, performance analyzer, and so on
StarTree Platform: a collection of services that provide various capabilities like
Management of other components: Responsible for deploying and managing the other components mentioned above. In addition, it is also responsible for pulling the latest releases and config updates from the control plane as and when required.
Security: Users can configure a custom OIDC-compatible Identity Service Provider (IDP) for administering how users and applications are authenticated before accessing the data plane. In addition, StarTree also provides a Role Based Access Control (RBAC) capability for configuring access control policies across different components.
Observability: Each data plane comes with built-in monitoring including a Grafana dashboard, for tracking critical system metrics (eg: Pinot query performance).
Metrics: Various metrics from the data plane are exported back to the control plane in a secure manner.
Fig 4: StarTree Data Plane services (Data Manager, ThirdEye, MyApps)
Control Plane
The StarTree Control plane is responsible for the provisioning and management of StarTree environments (aka data plane) across different cloud providers and regions. It provides different functionality depending on the user persona as mentioned in detail as follows.
Customer Admins
Customer admins use a self-service cloud portal UI (in private preview) to manage the entire lifecycle of a data plane. This portal guides them through the provisioning flow which includes configuring:
Deployment Model: Public SaaS or BYOC
Choice of Cloud Provider: AWS, GCP, or Azure
Identity Service Provider (IDP) of the data plane
Pinot cluster sizing: number and type of broker nodes, number and type of storage nodes
Other advanced configurations (networking, region, availability zones, security, and so on)
Once the environment is provisioned, admins can also manage the environment including things like:
Upgrading component versions of the corresponding data plane
Pinot Cluster capacity planning (scale-up/scale-out)
Generating API keys
StarTree Admins and Operators
The control plane is also responsible for fleet management of the various data planes deployed. This includes things like:
Metrics aggregation and Alerting
Status check of each data plane
Changing any of the configs mentioned above.
Security Considerations for BYOC
Providing a fully managed experience for the data plane is quite challenging in a BYOC scenario. The control plane often needs to provision new resources, shuffle data around, replace unhealthy servers, collect metrics and so on which requires direct access to the data plane. For instance, in AWS, the StarTree account will need permissions on EC2, S3, Networking, EKS, AutoScaling and IAM. Needless to say, providing such an elevated set of permissions to a StarTree assumed role or service is less than ideal.
To overcome this, we follow the Principle Of Least Privilege (POLP) where the rights of StarTree users/systems are restricted to the minimum access required. This is implemented via a unique deploy-manage permission model as shown below. 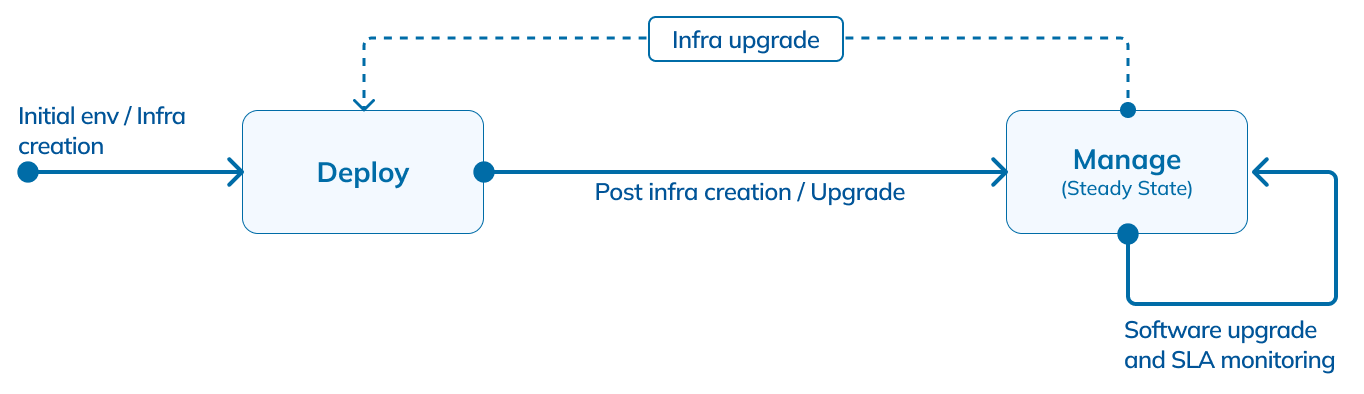
Fig 5: StarTree role state machine
As the name suggests, the StarTree account assumes the `deploy` role with permissions to provision infrastructure in the customer’s account. Once the environment is set up, we switch to a `manage` role with the bare minimum scoped-down permissions for the resources created as part of the deployment and nothing else. Throughout the lifecycle of this cluster, StarTree uses the ‘manage’ role for routine maintenance. In some rare situations, we might need to switch back to the ‘deploy’ role (e.g. Infrastructure upgrade) which is gated behind the customer’s consent and approval.
At a high level, we’ve designed the end-end architecture to ensure:
No inbound access into the cluster from the control plane for software upgrades. Control Plane uses cloud provider APIs to communicate with the cluster securely without need for opening any port in the data plane.
All software and configuration changes can be initiated from the control plane without needing any direct access to the environment
No access to customer’s data in the data plane.
The Customer has full control over StarTree’s access via cross-account IAM roles.
Summary
As you saw in this blog, both Public and BYOC deployment models guarantee data security for StarTree Cloud users. At the same time, the BYOC edition gives them more control over their data, leading to simpler governance and compliance certification. In addition, having the same building blocks helps in accelerating our development velocity across these offerings.
| BYOC (Private SaaS) | Public SaaS | |
| Fully Managed | Yes | Yes |
| SLA guarantees | Yes | Yes |
| 24x7 support | Yes | Yes |
| Provisioning complexity | Easy | Easy |
| Authentication and Authorization | Supported | Supported |
| Isolation Guarantees | Supported | Supported |
| Data management and Security | Data never leaves customer’s compliance boundary | Stored securely in StarTree operated clusters |
| Data Governance and compliance | Flexible: customer dictates the policies | Standard |
| Infrastructure customization | Broader range of compute and storage types to choose from | Standard compute and storage instance types |
| Cost Optimizations | Can apply customer cloud account for improved discount/savings | Standard: Uses StarTree Cloud account for cloud provider |
Next Steps
Intrigued to try out StarTree Cloud? Now’s your chance! Sign up for a 30-day free trial of our Public SaaS offering. You can also order it directly from AWS or Azure marketplaces. Also, make sure to bring your questions to our Slack community.
StarTree Cloud